Anarchy Panel

what is Anarchy Panel
Anarchy Panel is a dangerous tool in the cyber world that allows hackers to gain unauthorized access to infected systems and take control of them. Anarchy Panel 4.7 malware is particularly designed for Windows systems and aims to execute various cyber attacks, including stealing sensitive information, collecting data, and stealing cryptocurrencies and bank accounts.
main purpose of the Anarchy Panel Malware
Anarchy Panel Android banking malware is primarily a ransomware targeting sensitive user information, bank account details, and access to digital currency wallets. This malware, with its features, allows hackers to indirectly take control of infected devices and steal users’ financial information without their knowledge.
How is Anarchy Panel 4.7 different from other Banking malware
A regular Trojan and the Anarchy Panel banking malware are both types of ransomware that infiltrate computer systems, but their goals and functions are different. A regular Trojan typically masquerades as useful and harmless software, and after installation, it engages in stealing information, spying, or damaging the system. On the other hand, Anarchy Panel is specifically designed to target banking information, attempting to directly compromise the financial integrity of users by stealing account data and financial details. While Trojans usually operate without drawing attention, the Anarchy Panel banking ransomware often employs more methods to deceive users, such as sending phishing emails or using fake websites. Thus, while both types of malware pose serious threats to cybersecurity, they have significant differences in terms of objectives and execution methods.
How not to get infected with Anarchy Panel
To prevent infection from banking trojans, including Anarchy Panel, you can take the following measures:
- Install and Update Antivirus: Always use reputable antivirus software and update it regularly.
- Be Aware of Suspicious Emails and Links: Never click on unknown links or suspicious attachments. These links are often found in phishing emails.
- Use Strong Passwords: Use strong and unique passwords for your banking and online accounts, and enable two-factor authentication if available.
- Protect Your Personal Information: Never enter your personal or banking information on untrustworthy websites.
- Update Your Operating System and Software: Keep your operating system and software up to date to prevent new security vulnerabilities.
- Familiarize Yourself with Signs of Banking Trojans: Be aware of the signs of infection by banking trojans and suspicious behavior of software. If you suspect your system is compromised, take immediate action.
By following these tips, you can minimize the risk of being infected by banking trojans.
Is working with Anarchy Panel easy
Anarachy Panel 4.7 has a very graphical and simple management panel that is easy to use for everyone. This panel has a stylish and user-friendly design that can easily access all the features. Therefore, it is one of the best and most advanced botnets.
How to download Anarchy Panel
You can download Anarchy Panel by visiting the link below and purchase the latest version along with a video tutorial. Also, after saving, the new version will be sent to you for free. If you are installing or running Anarchy Panel 4.7, you cannot send us a message through support or Telegram to fix your problem.
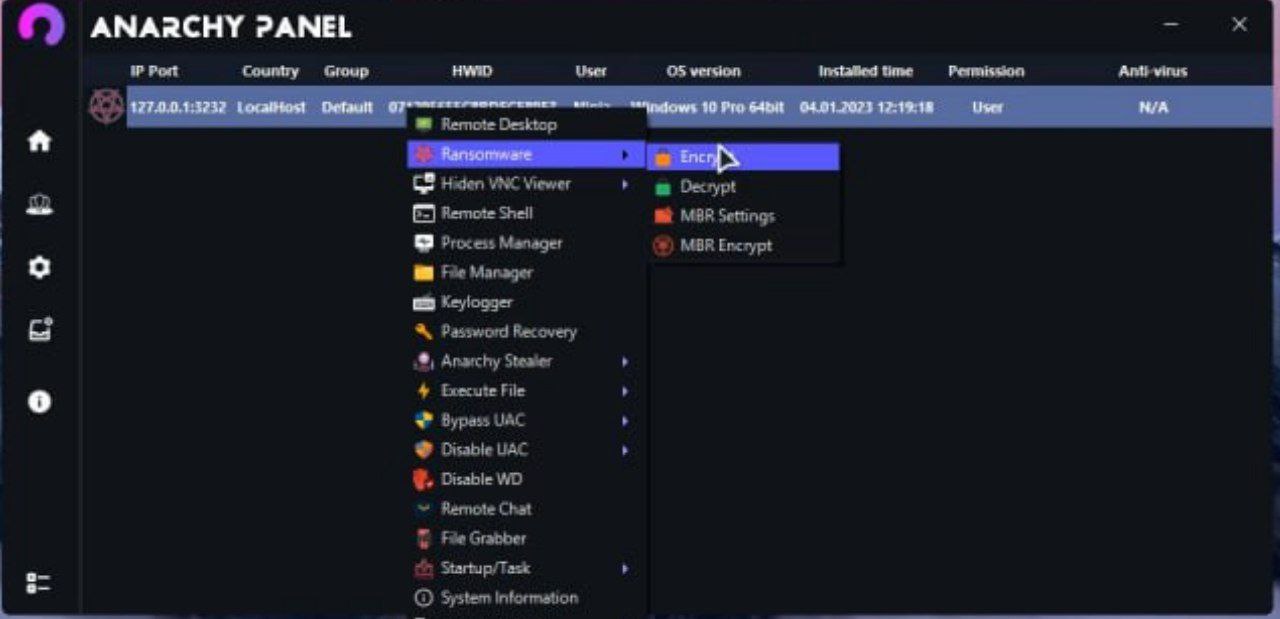
Anarchy Panel 4.7 Ransomware: An Overview of Cyber Threats
The Anarchy Panel ransomware is a specific type of cyber threat designed for extorting individuals and organizations. This type of ransomware possesses unique features that distinguish it from other kinds of ransomware, enabling hackers to access sensitive information from victims and demand ransom.
initiating the Attack:
Anarchy Panel 4.7 ransomware typically infiltrates victims’ systems through common attack methods such as phishing, exploiting software vulnerabilities, or even through downloading malicious software. Once this ransomware gains access to the victim’s system, it quickly begins encrypting files and important data.
Data Encryption:
One of the prominent features of Anarchy Panel 4.7 is its strong encryption method. This ransomware usually employs complex algorithms for encryption, making it impossible to recover data without the decryption key. This situation puts immense pressure on victims to pay the ransom promptly.
Displaying the Ransom Note:
After encrypting the data, Anarchy Panel 4.7 ransomware displays a message on the screen that includes the ransom demand details, typically in cryptocurrency (such as Bitcoin). This message also contains instructions for payment and threats regarding the permanent deletion of encrypted data if the ransom is not paid.
Role of the Management Panel:
A unique aspect of Anarchy Panel v4.7 is that hackers can track the attack’s progress and the payments made through a specific management panel. This panel allows them to provide updates on the victims’ statuses and ensure ransom payments are received. This method aids in empowering hackers while keeping them hidden from law enforcement.
Economic and Social Impacts:
Ransomware attacks like Anarchy Panel not only lead to economic damage for victims but can also have negative social effects. Such attacks create fear and anxiety among users and organizations and can contribute to a decrease in public trust in online services and information systems.
Prevention and Response:
To prevent Anarchy Panel ransomware attacks and similar threats, users and organizations need to adopt strong security measures. These measures may include regular software updates, effective antivirus software, regular data backups, and training users on how to recognize phishing methods.
Conclusion:
In conclusion, Anarchy Panel ransomware represents a serious threat in the cyber world. With the increasing use of technology and the internet, awareness of these threats and adopting necessary measures to protect sensitive data and information is essential. In facing such threats, users and organizations must maintain collaboration, preparedness, and appropriate crisis management strategies to prevent serious financial and operational damages resulting from ransomware attacks.

